Dell EMC PowerProtect Cyber Recovery
Why is it necessary?
According to Gartner, “Ransomware is one of the most dangerous threats to organizations, but the nature and scope of ransomware attacks are often misunderstood, leading to inadequate precautions against ransomware and flawed responses to successful attacks.”
Increasingly sophisticated ransomware attacks are specifically targeting backup data and administrator functions,” and in today’s environment Gartner suggests that “you can never be 100% certain that backup data isn’t infected with malware and must proceed from the assumption that backups have been affected."
Regardless of the focus or size of an agency, cyber-attacks continually expose governments to compromised data, lost productivity due to downtime, and reputational damage. Because of this, having a cyber recovery strategy has become a mandate for government leaders.
What can I do to protect my agency?
In response to the threat of increasingly sophisticated ransomware, with attacks being launched by criminal and governmental organizations worldwide, Gartner has provided 4 key recommendations for data protection leaders:
• Eliminate simple network sharing protocols.
• Protect the backup system — both the backup administration console and copies of backup data.
• Use multifactor authentication for administrative accounts.
• Create an isolated recovery environment.
The question you and your IT staff need to ask is: Does your organization have a comprehensive cyber recovery plan?
Four Points Technology, a Dell Technologies Gold Partner, agrees with the Gartner report and recommends Dell EMC PowerProtect Cyber Recovery to address each of Gartner’s recommendations, and more.
How will Dell EMC PowerProtect Cyber Recovery protect critical data from ransomware across on-premises and multi-clouds?
| 5 Components | PowerProtect Cyber Recovery |
|---|---|
| Data Isolation and Governance An isolated data center environment that is disconnected from corporate and backup networks and restricted from users other than those with proper clearance. |
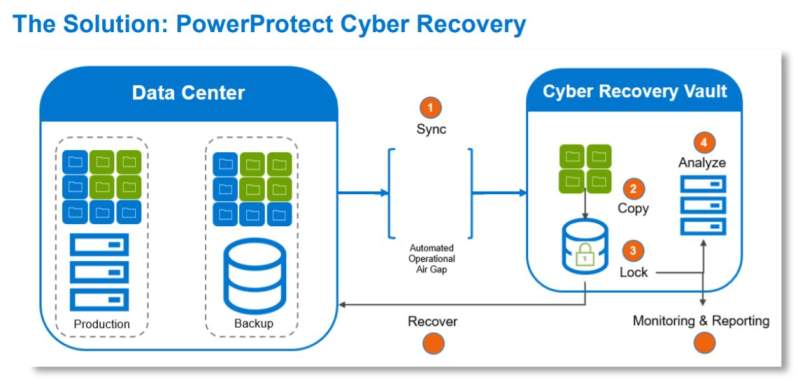
The PowerProtect Cyber Recovery vault offers multiple layers of protection to provide resilience against cyber-attacks even from an insider threat. It moves critical data away from the attack surface, physically isolating it within a protected part of the data center and requires separate security credentials and multifactor authentication for access. |
| Automated Data Copy and Air Gap Create unchangeable data copies in a secure digital vault and processes that create an operational air gap between the production / backup environment and the vault. |
PowerProtect Cyber Recovery vault also has additional safeguards include an automated operational air gap to provide network isolation and eliminate management interfaces which could be compromised. PowerProtect Cyber Recovery automates the synchronization of data between production systems and the vault creating immutable copies with locked retention policies. If a cyber-attack occurs, you can quickly identify a clean copy of data, recover your critical systems, and get back up and running. |
| Intelligent Analytics and Tools Machine learning and full-content indexing with powerful analytics within the safety of the vault. Automated integrity checks to determine whether data has been impacted by malware and tools to support remediation if needed. |
PowerProtect Cyber Recovery is the first solution to fully integrate CyberSense, which adds an intelligent layer of protection to help find data corruption when an attack penetrates the data center. This innovative approach provides full content indexing and uses machine learning to analyze over 100 content-based statistics and detect signs of corruption due to ransomware. CyberSense finds corruption with up to 99.5% confidence, helping you identify threats and diagnose attack vectors while protecting your mission-critical content – all within the security of the vault. |
| Recovery and Remediation Workflows and tools to perform recovery after an incident using dynamic restore processes and your existing DR procedures. |
PowerProtect Cyber Recovery provides automated restore and recovery procedures to bring mission-critical systems back online quickly and with confidence. As part of PowerProtect Data Manager and for customers running Dell EMC NetWorker, Cyber Recovery enables automated recovery from the vault. Dell EMC and its ecosystem partners provide comprehensive methodology for protecting data, as well as performing damage assessments and forensics to either recover your systems or remediate and remove the offending malware. |
| Solution Planning and Design Expert guidance to select critical data sets, applications, and other vital assets to determine RTOs and RPOs and streamline recovery. |
Optional Dell EMC Advisory Services can help you determine which mission-critical systems to protect and can create dependency maps for associated applications and services, as well as the infrastructure needed to recover them. The service also generates recovery requirements and design alternatives, and it identifies the technologies to analyze, host, and protect your data, along with an implementation timeline. |
With Multi-Cloud Data Services for Dell EMC PowerProtect, you get a data vaulting service that offers an air-gapped vault built upon secure, multi-cloud-enabled infrastructure to safeguard your critical data from cyber-attacks.
A PowerProtect Cyber Recovery vault environment is hosted in Faction with multiple levels of physical and logical protection and flexible recovery options to ensure you can recover your data with confidence.
Protecting your vital data from cyber-attacks requires proven, modern, and intelligent solutions that can isolate critical data, identify suspicious activity, and accelerate data recovery. Dell EMC PowerProtect Cyber Recovery can give you confidence that you can quickly identify and restore known good data and resume normal operations after a cyber-attack.

Power2Protect Podcast
Tune in to hear Dell Technologies cyber resilience experts discuss why U.S. Federal Reserve Chairman, Jerome Powell called cyber-attacks, “the #1 threat to the global financial system”.
Plus, get practical tips on how to protect, isolate and recover critical data from ransomware across edge, core, and cloud with PowerProtect Cyber Recovery.
Listen Now »

Founders Federal Credit Union Achieves Its Mission with Dell EMC Data Protection
Founders FCU’s CTO, Bob Bender, understands that timely access to “pristine data” is the key to achieving his organization’s mission.
Learn how utilizing Dell EMC PowerProtect Cyber Recovery and PowerProtect DD gives Bob’s team, his leadership, and his customers confidence by knowing their valuable financial data is protected from ransomware and cyber-attacks.
Watch Now »
Ready to talk to Four Points Technology about your Cyber Recovery Plan?
For additional information, please contact cybersales@4points.com






